Post-Hack Response
What to Do if an Admin Gets Compromised
Discord Security Tip
What to do when the worst happens and your Discord server does get compromised? This thread will cover what you should do as an admin or a server owner during all stages of a Discord compromise and fake mint/airdrop phishing scam.
First, take a screenshot of the fake announcement - we will need this for later. Try to delete the fake announcement, follow this up by banning the user who was posting the announcement. Go to Server Settings->Integrations, remove all webhooks.
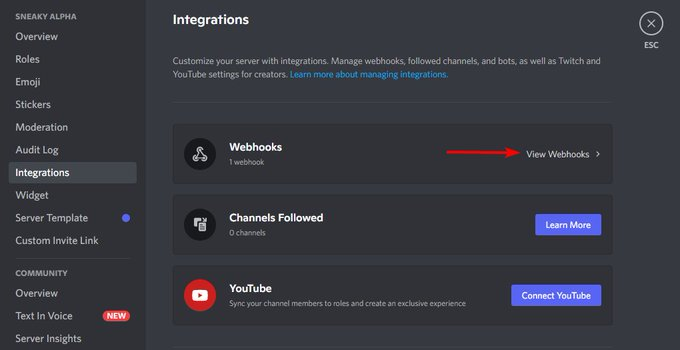
Send a message to all of your team members/moderators to change their password immediately. Best if sent not over Discord DM. If you were unable to ban the user who was compromised, you need either the server owner to ban them or for the user to change their password.
Next - review all roles, look for any roles with dangerous perms (admin/webhook/roles) toggle them off by hitting clear permissions. The attackers will give roles to their alts, to keep the attack ongoing for as long as possible. Removing perms is fastest way to deal with that.
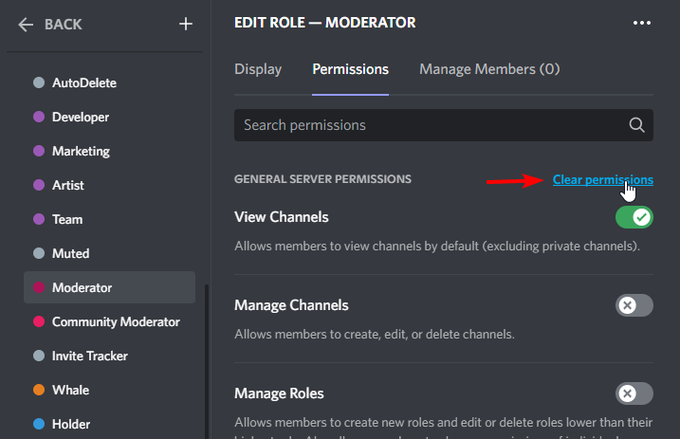
While going through roles, remove all permissions from Bot roles as well. This will bypass any malicious bots or changed Bot settings - we will still review changed settings but this is the fastest way to react. Bots could be used to re-role users or potentially change perms.
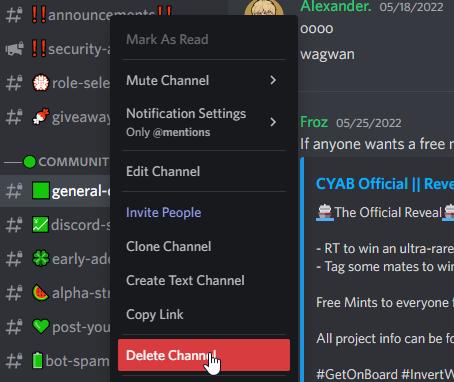
Delete your announcement channel. Because of how Discord works, sometimes the scam messages will still appear for people when they first open their Discord. Deleting the announcement channel is the only way to limit more losses. Check webhooks one more time after doing this.
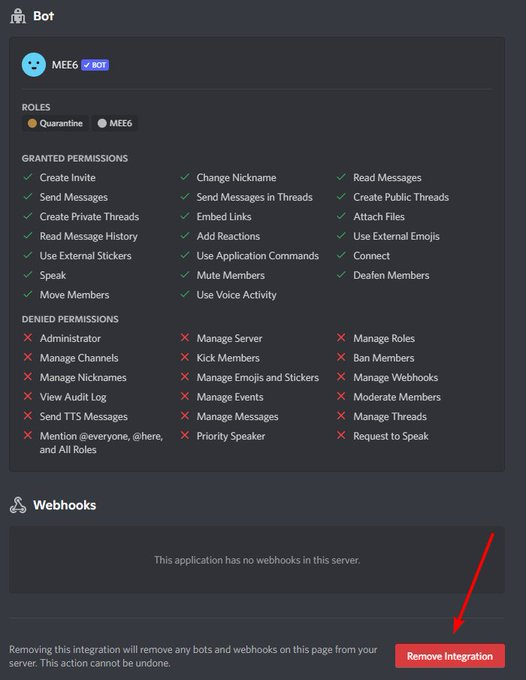
Go back to Server Settings -> Integrations. Review all installed Bots. Anything added within a day or two, click manage, and then remove integration. Attackers occasionally will install their own bots on the server, we must remove these (even though they are now powerless).
Next we need to go to Server Settings -> Audit Log Scroll back to when the attack started, and look through what the compromised account changed, any alts that were granted roles, ban those accounts. Make a short note of anything modified so you can check it later.
For any Bot in your server that had any elevated permissions (manage roles, admin, etc). Visit the dashboard, check built in logs to see what settings were changed. If the bot does not have a log, consider removing the bot or review all the settings manually.
Following the audit log review: 1. Check perms on any roles changed (that you didn't already clear perms on) 2. Check perms on any channels changed - if they changed perms on all channels, drag channels to an archive category with no permissions on it and sync channels to it.
Remove all Team members from their (now powerless) roles, grant their roles back later after they confirmed on a different avenue of communication that they changed their password.
After the attack... Go to Server Settings -> Custom Invite Link Ensure your Vanity URL was not changed, if it was, update your public facing Discord invite link and message Discord's customer support. Check all your non-vanity public invite links, make sure they're all good.
Give Team/Mod roles back minimum permissions needed until full review of server is completed. Re-add team members who changed their password to their old roles. Make a new fresh announcement channel (don't clone!) and post an announcement explaining the situation. Communicate.
Review your screenshot you took of the fake announcement - on a different device not connected to your Discord account, go to the fake site, initiate a transaction (don't sign it obviously) so you can figure out the attacker's wallet. Write down the wallet somewhere.
Post on Twitter as well that there was a compromise and that the server is back under control. Post resources for your affected community members to understand how to revoke approvals (psst: https://twitter.com/Jon_HQ/status/1534261731152695297) Set up a meeting with the team to talk about next steps.
Restitution + Next Steps Get some sleep. This is an incredibly stressful situation and will cause anyone to start making mistakes after dealing with it. Once you got some rest, there are a couple options about how to deal with community members who lost funds or NFTs:
1. Do nothing. Don't pay them back. This will look incredibly poorly on your project. Even if you're pre-mint, or your company isn't doing an NFT sale, there are other options you can take to try to make it up to the community. An NFT project is its community. Endstop.
2. Pay back just ETH lost in the scam This is less and less of an option as scammers switch almost exclusively to NFT drainer websites. Most of the value stolen now from scams are through stolen NFTs, not transferred ETH. But for a project with limited funds this could work.
3. Pay back all funds lost This is the hardest pill to swallow. But if you go down this path, the number 1 thing I recommend is to have your restitution form be through @PREMINT_NFT - you can verify their Discord/Twitter/Address all at once. Manually review each entry. Make sure each person is legit. Make sure they post on Twitter, they didn't join your Discord a day ago. You want restitution to go back to victims, not alt accounts potentially owned by the phishers. Past that - put a time cap on your restitution process, just to have an end.
4. Issue an NFT or grant WL spots to victims If you're pre-mint/don't have funds to issue full refunds, you can grant victims additional WL allocation or even give them a free mint NFT to hopefully recover some funds lost. This obviously throws a hitch in a project's plans.
After you as a team have formed your restitution plan - it is incredibly important to figure out how the team member who got compromised got phished. If it is not something apparent like a bookmarklet scam, scanned QR code, or screenshare. Reach out to a professional to review.
There is a small but real potential that they were hit with malware or something similar. Until the source of the compromise is found, assume they will remain compromised until it is discovered or they do a full computer wipe. I cannot stress this enough.
Lastly - after all of the above... The other thing you should do is focus on making sure this never happens again. Reach out to a @server_forge approved Discord auditor (like me!). And have someone review your server and set up safeguards to prevent this from happening again.
Checklist if a Mod Compromise Occurs
What do you do if your Discord server is being hacked, a checklist.
I'll post this both as a Twitter thread, and as an image attached to this tweet. Download the image and save it to share with teams, or print it out!
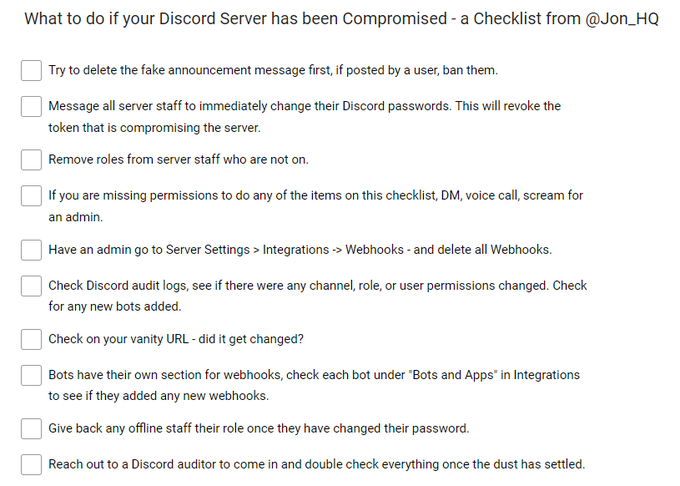
☐ Try to delete the fake announcement message first, if posted by a user, ban them. ☐ Message all server staff to immediately change their Discord passwords. This will revoke the token that is compromising the server. ☐ Remove roles from server staff who are not on.
☐ If you are missing permissions to do any of the items on this checklist, DM, voice call, scream for an admin. ☐ Have an admin go to Server Settings > Integrations -> Webhooks - and delete all Webhooks.
☐ Check Discord audit logs, see if there were any channel, role, or user permissions changed. Check for any new bots added. ☐ Check on your vanity URL - did it get changed? ☐ Bots have their own section for webhooks, check each bot under "Bots and Apps" in Integrations.
☐ Give back any offline staff their role once they have changed their password. ☐ Reach out to a Discord auditor to come in and double check everything once the dust has settled. For the compromised user, I go into more details in this thread: https://twitter.com/Jon_HQ/status/1490108397047271424
Additionally not mentioned above, if you are the server owner SHARE YOUR PHONE NUMBER WITH THE TEAM. They should be able to call you if the worst happens.
How Revoke.Cash Works (Share This With Your Community if They Ever Need to Revoke)
NFT Security Tip
How to revoke token approvals... what token approvals are... and how to figure out if you got compromised. Lots of technical stuff in here but I'll try to keep it super simple. This will be a comprehensive guide built for after attack response.
There are three main types of wallet compromises here: Transfer - you have lost whatever NFT you signed away. Token Approval - you gave attacker access to move your NFT, can be revoked. Seed Phrase lost - your entire metamask is no longer usable.
I will be covering the first two in this thread. If you gave away your seedphrase, there is not anything you can do to make your wallets safe again. Make a new metamask wallet, with a new seed phrase, and transfer anything in those old wallets to the new fresh account.
In any computer program or script, there are things called 'functions' - these basically are the actions you can make the program do. These are the ERC721 functions (or things you can do with an NFT contract) that we will be looking at specifically. I'll explain each.
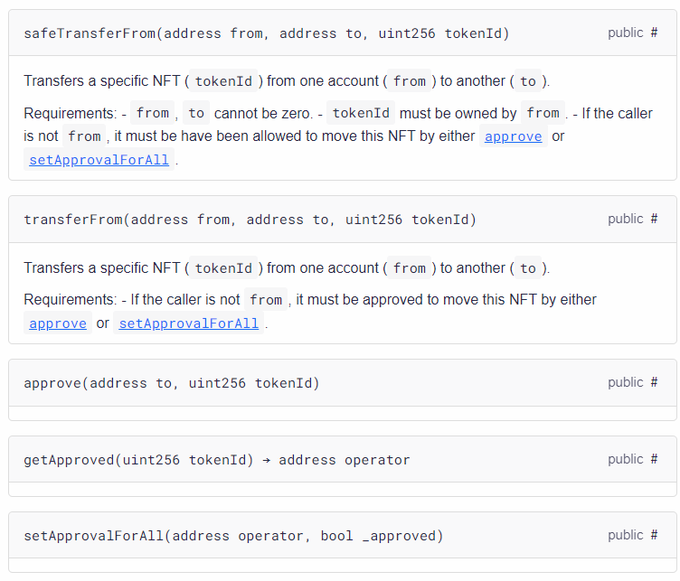
safeTransferFrom and transferFrom are the actions which actually move your NFT. If you see either of these actions have executed successfully from your wallet, the NFT is gone. Look on Etherscan for something like this:
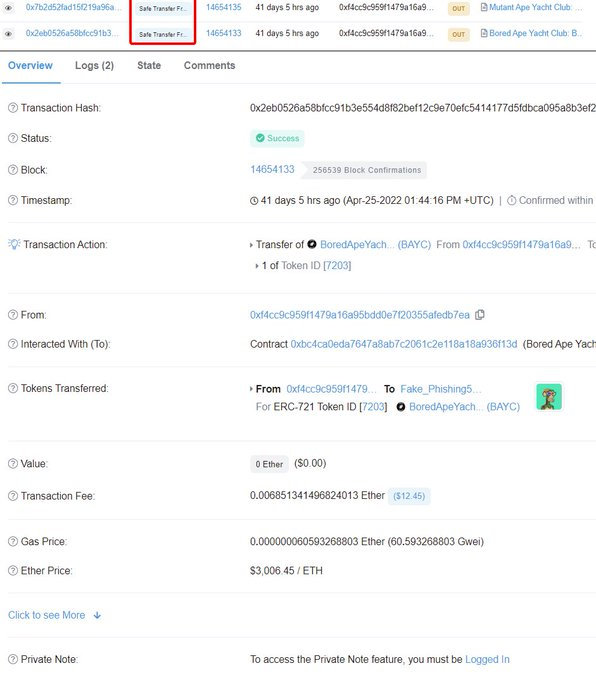
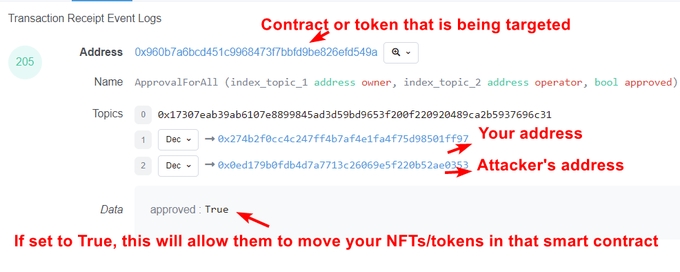
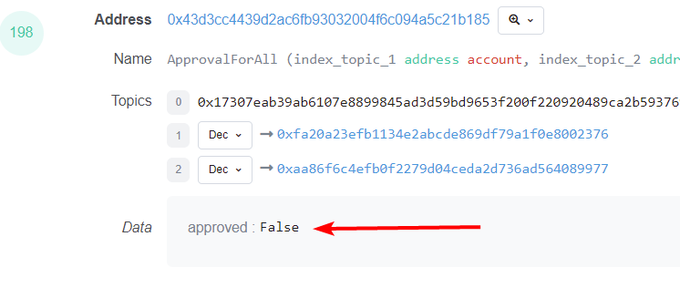
If you go to the Logs section on Etherscan you can see that this contract interaction did two things. Set approval (not really necessary since the owner of the NFT was executing this function). And then transfers the NFT to the attacker's wallet.
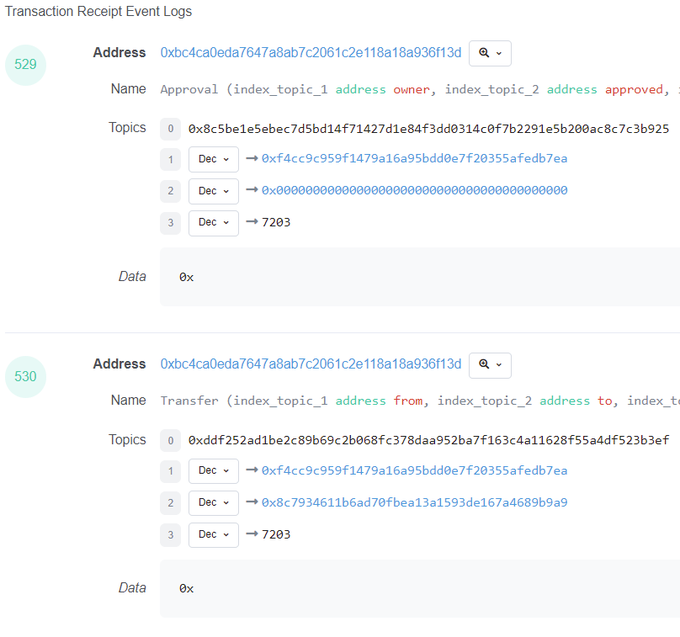
Using a transfer is something that I don't see often with attacks. As you can see in a MetaMask pop up, it states pretty clearly it's a transfer request Check the data tab, and you can see the function more clearly. If a minting website uses a transfer function, run away.
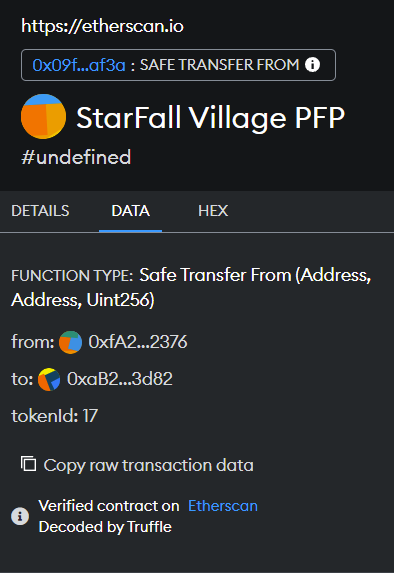
Instead what the attacker will do is only set the approval function. This might be SetApprovalForAll or even just Approval. This looks less suspicious and once you sign this and it hits the blockchain, the attacker can transfer your NFT without you signing anything more.
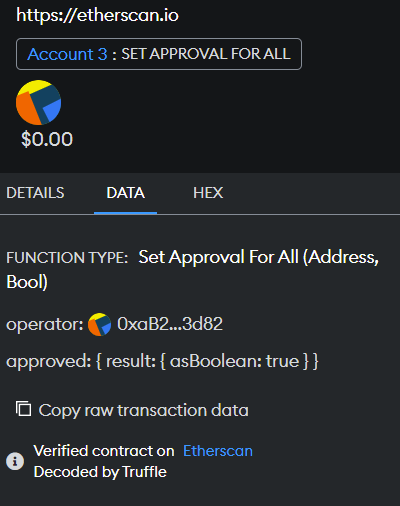
Here is the first step we will take to check if your wallet got compromised. Go to Etherscan and check your wallet's history. We're looking for this: If you see a Set Approval function anywhere, you signed a transaction to give the attacker access to your NFT or tokens.
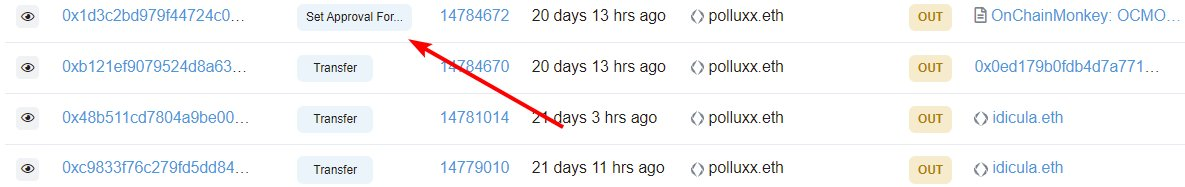
Click into the transaction and go to the logs section. Click on the first address, that will show you what NFT they targeted. If you see transactions like this, that you did not mean to do, we need to revoke. Until it is revoked your NFT can be moved without your say.
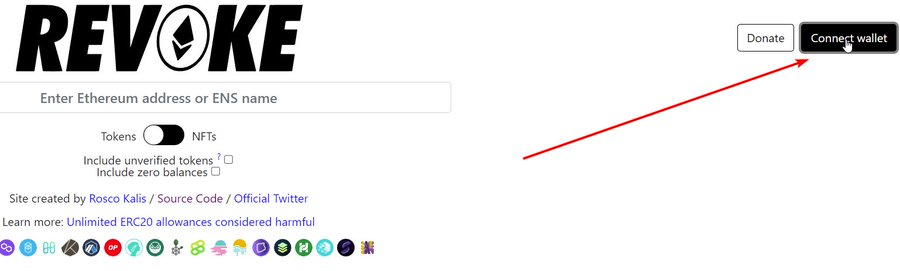
Now, let's go through step by step how to revoke token approvals. Let's start with the easiest one, http://revoke.cash After an attack, people will try to post scam revoke cash links, always type in the URL yourself Visit the site, connect your affected wallet.
If you found token approvals (Like WETH, USDC, etc) in your Etherscan when you reviewed the above click on the revoke button on each token that was approved by the attacker. Then switch to the NFTs tab, turn on zero balances, and revoke access to each NFT that was approved.
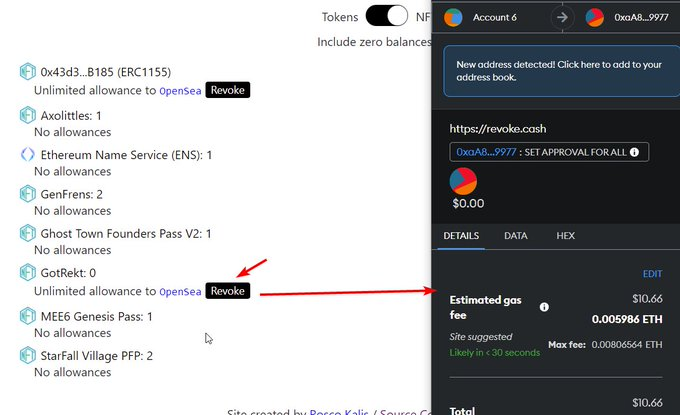
After you have revoked any approvals that the attacker made, go to Etherscan and wait until the transaction succeeds. Go to logs, and check if the data section says False. It is revoked! You can skip zero balance revokes if you won't use this wallet again.
14/16 - Etherscan also has a token approval checker here: https://etherscan.io/tokenapprovalchecker… To use their tool, click the Connect to Web3 button to link your compromised wallet.
ERC-20 tab will list your defi tokens,
ERC-721 tab will list NFTs,
ERC-1155 tab will list NFTs.
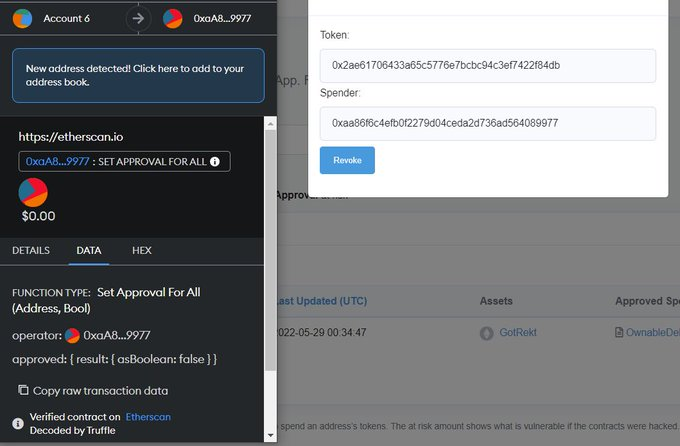
Click Revoke, and then sign the transaction request, if you go to the Data tab then you can see this will set it to false! Again - once you complete the transaction, go back to Etherscan and check your wallet, make sure the transaction completes.
There are many other ways and tools (@gemxyz is working on one!) for you to revoke approvals, but the two above are pretty simple and should work for you quickly. My biggest recommendation, is go through the steps above if you never had, and practice revoking approvals.
If you enjoyed this thread and want to read some other thoughts I have about securing NFT projects, I posted a recent thread that goes pretty in-depth into combating Discord impersonation: https://twitter.com/Jon_HQ/status/1531362140329652224… Thanks for reading!

Member discussion